Featured
Table of Contents
What Is A Vpn And How Does It Work?
Using other internet browsers and other web uses outside the web browser (e. g. online video games) can not be secured by the VPN. While internet browser extensions are not quite as detailed as VPN clients, they might be an appropriate choice for occasional internet users who desire an additional layer of internet security. They have actually proven to be more vulnerable to breaches.
Information collecting is the collection of personal information, such as what marketing strategists do to produce an individual profile of you. Marketing content is then personally tailored to you. If several devices are linked to the exact same web connection, it may be much easier to carry out the VPN directly on the router than to install a separate VPN on each device.
Yes, there are a number of VPN options for mobile phones and other internet-connected gadgets. A VPN can be essential for your mobile phone if you use it to save payment details or other personal information and even simply to surf the web. Numerous VPN companies likewise use mobile services - much of which can be downloaded straight from Google Play or the Apple App Store, such as Kaspersky VPN Secure Connection.
While they secure your IP and encrypt your internet history, a VPN connection does not safeguard your computer from outside intrusion. To do this, you must definitely utilize anti-virus software such as Kaspersky Internet Security. Since utilizing a VPN on its own does not secure you from Trojans, viruses, bots or other malware.
What Is A Vpn And How Does A Vpn Work?
As currently discussed, there are likewise VPN connections for Android mobile phones and i, Phones. Thankfully, smart device VPN services are simple to utilize and normally include the following: The installation process generally only downloads one app from the i, OS App Shop or Google Play Shop. Although free VPN suppliers exist, it's a good idea to select an expert company when it pertains to security.
The majority of apps will then guide you through the essential functions of the VPN services. Changing on the VPN literally works like a light switch for numerous VPN apps.
A VPN is only as protected as the information use and storage policies of its service provider. Bear in mind that the VPN service transfers your information to their servers and these servers link over the internet on your behalf. If they save information logs, make sure that it is clear for what function these logs are kept.
Anything that does not utilize a cellular or Wi-Fi connection will not be sent over the internet. As an outcome, your VPN will not secure your basic voice calls or texts.
It's Time To Stop Paying For A Vpn
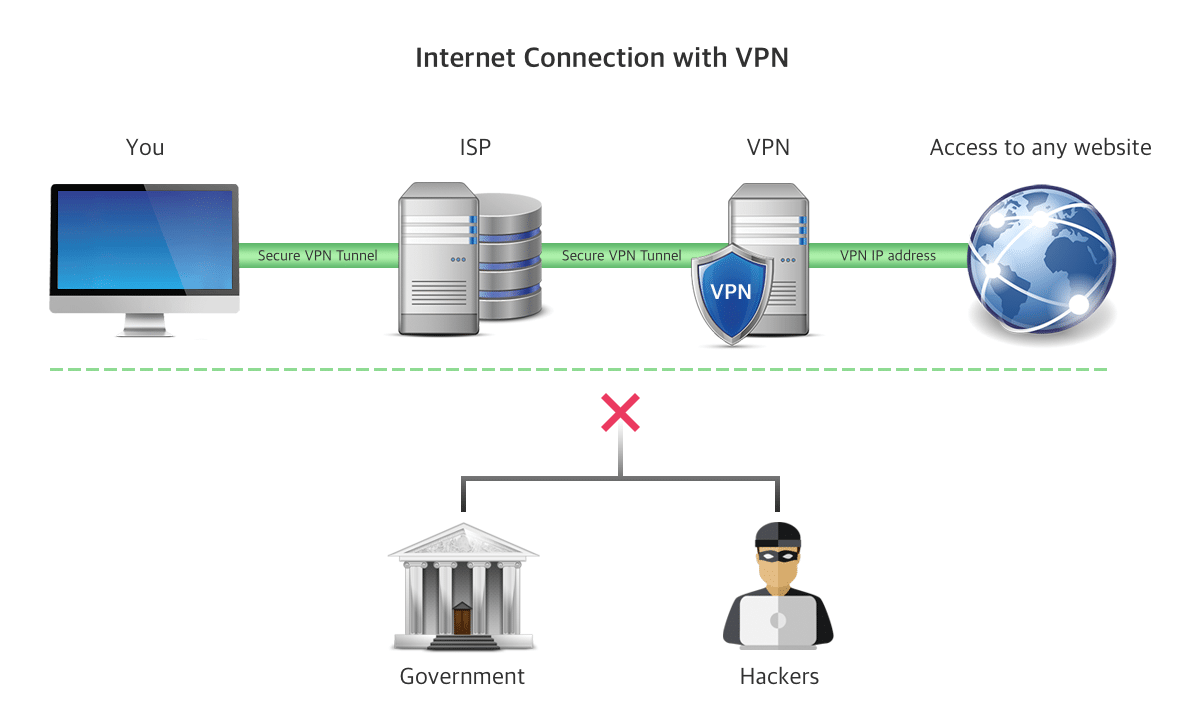
The VPN connection does not secure you from hacker attacks, Trojans, viruses or other malware. You should for that reason rely on an additional trusted anti-virus software application.
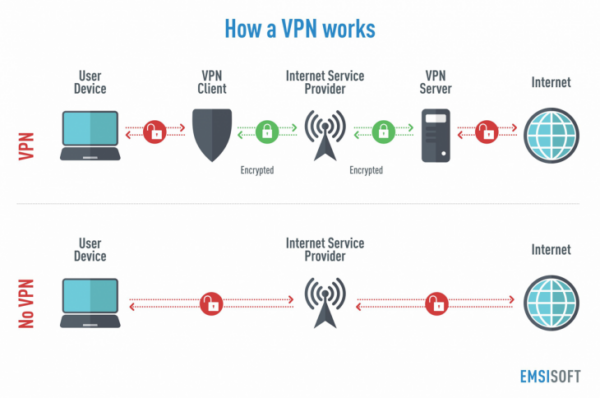
Anyone on the exact same network will not be able to see what a VPN user is doing. This makes VPNs a go-to tool for online personal privacy.
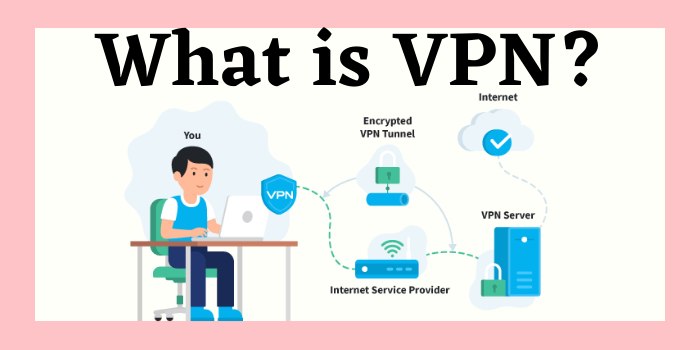
The VPN client is not obvious to the end user unless it creates performance concerns. By utilizing a VPN tunnel, a user's device will link to another network, concealing its IP address and securing the information. This is what will hide private info from assailants or others wishing to get to an individual's activities.
VPNs associate a user's search history with the VPN server's IP address. VPN services will have servers situated in various geographical locations, so it will look like the user might be from any one of those areas. VPNs can impact efficiency in lots of methods, like the speed of users' web connections, the procedure types a VPN supplier can utilize and the kind of encryption used.
What Is Vpn And How Does It Work
If the VPN connection is disrupted, the kill switch will instantly detach the gadget from the web to get rid of the chance of IP address direct exposure. There are two types of kill switches: avoid gadgets from connecting to unsafe networks when the gadget is linked to the VPN.

are more safe. They keep the device from connecting to non-VPN connections even while disconnected from the VPN server. VPNs are utilized for virtual personal privacy by both normal web users and companies. Organizations can use VPNs to make sure outdoors users that access their data center are licensed and using encrypted channels.
When surfing the web, a web user might know accessed by an assaulter, including browsing practices or IP address. If privacy is an issue, a VPN can offer users with peace of mind. Encryption, privacy and the ability to navigate geographically obstructed content is what most users find valuable in a VPN.
The challenges of utilizing a VPN, however, consist of the following: Not all gadgets might support a VPN. VPNs do not safeguard versus every hazard.
What Is A Vpn, And How Does It Work?
Network administrators have several alternatives when it comes to deploying a VPN that include the following. Remote access clients link to a VPN gateway server on the company's network. The gateway needs the device to validate its identity before granting access to internal network resources. This type generally depends on either IPsec or SSL to protect the connection.
Latest Posts
9 Best Vpns For Home And Business In 2022
12 Best Vpn Service Providers In 2023
Best Vpns For Freelancers And Remote Workers: Protect ...