Featured
Table of Contents
Difference Between Tor And Vpn
Do you ever wonder who can see your web traffic while surfing the web? If so, you're not alone.
By utilizing these tools, web users can utilize the web with boosted comfort. To assist you better understand these tools, here's what we'll cover in this guide: So, what are these tools and how do they work? To help you find which tool is best for you, continue checking out for a total breakdown of Tor vs.
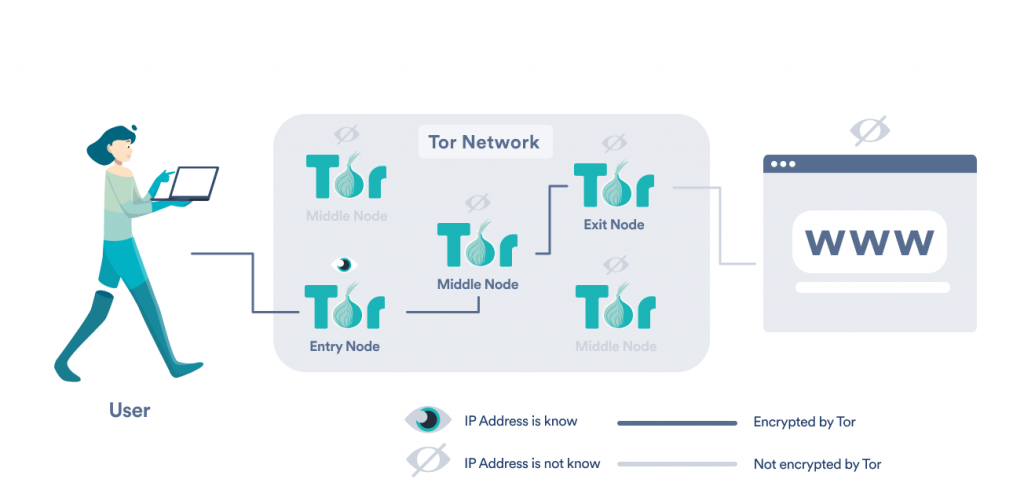
The guard node will be able to see your IP address, but it will not see the details of your request. The middle node then eliminates the 2nd layer of file encryption and sends your request to the exit node. Finally, the exit node eliminates the last layer of file encryption, allowing it to see your demand, although it will be not able to identify who requested it.
Vpn Vs Tor, Which Is Better? - Bitvpn Blog
The only way someone can identify your activity is if they happened to maintain both of the arbitrarily picked guard and exit nodes, which is extremely not likely. While using the Tor web browser has its benefits, there are advantages and drawbacks when it concerns utilizing Tor over a standard internet browser like Safari or Google Chrome.
Pros of utilizing the Tor browser: Free and easy to download: Thanks to various anonymous volunteers, users can quickly download and use the Tor web browser free of charge. Difficult to close down: The Tor network is run by thousands of volunteers all over the world, making it extremely challenging for a single entity to shut it down.
Bypass censorship: If you remain in a country with strict censorship, the Tor browser will enable you to bypass censorship and see obstructed websites. Access to the dark web: With the Tor internet browser, you have the ability to access sites on the dark web. These sites are also referred to as onion websites and can just be gone to using the Tor web browser.
Vpn Vs Tor: Which One Is Right For You?
Node vulnerability: Since the Tor web browser assists make your identity confidential, it does not bother securing your information after it leaves the exit node. This makes it possible for somebody monitoring your connection to see your traffic information, even if they do not know who it belongs to. Even with its advantages and disadvantages, there are certain situations in which using the Tor browser might be your finest option.
Now that you're mindful of the benefits and disadvantages of using Tor, you might be wondering when you should utilize it. Tor is finest for: Anonymous web browsing Accessing the dark web Untraceable interaction If your main concern is staying anonymous online or you want to access the dark web, then using the Tor internet browser might be your best bet.
This permits VPN users to travel the web privately and anonymously, no matter the internet connection. How does a VPN work?
Tor Vs. Vpn: Which Should You Choose?
This very same process takes location with the information returning to your gadget. Simply like using the Tor web browser, VPNs aren't ideal.
Follow along to find out when using a VPN is your best alternative. After discovering more about VPNs, you may be questioning when to utilize one. A VPN is best for: If you live somewhere with rigorous web censorship and often discover yourself utilizing public Wi-Fi connections, investing in a VPN service might be a great option.
Before picking a VPN or Tor, follow along to learn more about the key distinctions. One huge distinction in between a VPN and Tor is how they're handled. A VPN is a central service, indicating the VPN company is the sole authority, handling all servers and connections. In many cases, this is a personal business.
Tor Vs Vpn – What Is The Difference Between Them?
On the other hand, Tor is completely decentralized, and none of its servers are managed by a single entity. Instead, the decentralized network depends on its worldwide network of specific volunteers. Due to the fact that of this, it is a lot more hard for someone to trace your data or shut down the network.
Most VPNs direct your web traffic through a single server before it reaches its designated destination. This is referred to as a single-hop VPN. On the other hand, the Tor internet browser routes your web traffic through three random nodes. This complicated process makes your information inherently hard to trace. When it concerns choosing a VPN, you'll have many alternatives to choose from.
This grants you all of the personal privacy benefits of the Tor network and extra IP address defense from your VPN, avoiding your ISP from knowing that you utilize Tor and keeping any Tor node from seeing your IP address. Tor then VPN: Beginning with the Tor network is a challenging process and might not be supported by all VPN companies.
Vpn Vs Tor: Which One Is Right For You?
When you utilize a VPN, you need to rely on the VPN company. Due to the fact that each Tor node only knows the identity of the server before it, it is impossible for anybody to reverse engineer your connection's route through the Onion network. Tor also lets you access a variety of unlisted sites with the.
![Tor Vs. Vpn [2021] – Which Is Best?](https://www.firewall.cx/images/stories/vpn/tor-vs-vpn-guide/tor-vpn-understanding-comparing-tor-with-vpn-4.jpg)

VPNs don't require the very same level of technical proficiency as utilizing Tor does. You should still make sure to select a trustworthy, zero-logs VPN supplier that does not to leakage user information. If you're short on time, here are some quick answers to typical concerns asked about Tor vs.This makes VPNs the preferred method of bypassing geo-restrictions. The Dark Web (. onion websites) are just accessible through the Tor internet browser. However, users can opt to use a VPN with Tor for an extra layer of security.
Latest Posts
9 Best Vpns For Home And Business In 2022
12 Best Vpn Service Providers In 2023
Best Vpns For Freelancers And Remote Workers: Protect ...